Categories
Compliance, Standards, and Regulations Are Your Security Friends
June 9, 2017
Where should organizations look for guidance on what to do in order to be proactive about security?
For guidance in managing data protection, security, compliance, and governance on the cloud, companies should look to compliance laws, standards, and regulations. Doing so is the first step in defining a security and risk management strategy that is right for your organization, and then translating that strategy into concrete, actionable security controls for effective cloud security.
Standards are typically formed to address emerging bad practices or threats in industries. Because of this, they are designed with a few things in mind:
- Proactive controls that encourage organizations to focus on prevention for more comprehensive and resilient practices
- Uniform benchmarks of good practices, as data and consensus on these practices emerge in response to harmful activities
- Regulatory or community pressure that motivates organizations to take action
Some notable security and compliance bodies/regulations include:
- SOX – for protection against fraudulent business practices
- PCI-DSS – for the security of credit, debit, and cash card transactions and related personal information
- HIPAA – for the privacy and security of healthcare and patient data
- FFIEC – for the uniform supervision of financial institutions and their compliance with banking standards
- FISMA – for the protection of government information
- FedRAMP – provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services
Some notable standards include:
- DISA/NIST STIGs – highly specific configuration guidelines for locking down IT assets
- ISO2700X – best practice recommendations on information security management
- CIS Benchmarks – security configuration guidelines for locking down IT assets
- CVEs – reference for common information security vulnerabilities and exposures
While these standards and regulations vary in scope and focus, the point to remember is that the underlying actionable principles of these standards and regulations are common.
For example, the number of security controls varies between the frameworks below, but there is significant overlap in their content.
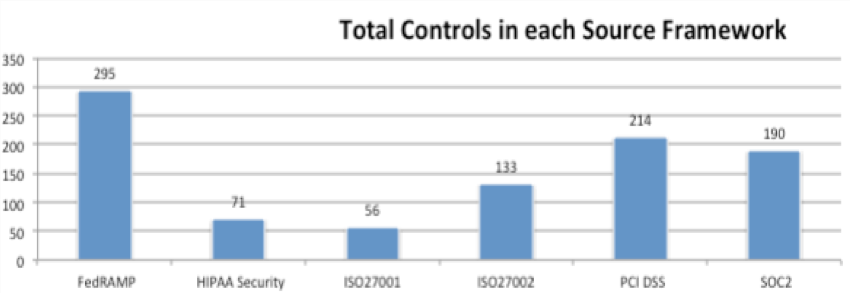
We can map the content of these frameworks to security control domains, like below:
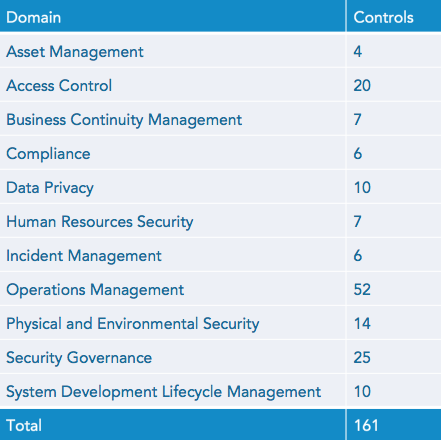
From this view, the underlying principles across frameworks become apparent. What’s also clear is that we can map these domains to specific security controls that are actionable. In our view, the DISA/NIST STIGs comprise the most stringent superset of these frameworks. We’re fans of the STIGs because they are highly concrete and specific in their descriptions, and are thus easy to translate to actionable security controls. By first defining common domains across frameworks, and then defining the specific controls that fall under each domain (by pulling from STIGS or other specific descriptions), we make cloud security actionable.
To summarize, compliance regulations, standards, and benchmarks are the key starting point in defining a proactive cloud security and risk posture for your organization, and then translating that posture to actionable security controls.
But knowing what to do is only half the battle; the other half of the battle is knowing how to deploy controls effectively at scale and throughout the various layers of an organization.
Where should organizations look for guidance on how to deploy a proactive security and risk posture?
Once an organization has defined a security and risk posture and identified the actionable security controls needed to deploy that posture, how exactly do they go about doing that? That’s where creating security profiles and automating their application comes in. In our definition, a security profile is a set of concrete, actionable security controls that are grouped together for a specific purpose, system, or application. For example, you can have a security profile called “PCI-DSS MySQL Database Profile” that includes all the controls needed to make a cloud-based MySQL database compliant with PCI-DSS regulations.
The power of a security profile is that it allows you to correlate specific controls with specific objectives of your organization’s security posture and risk management strategy. For example, organizations often need flexible security during development, and then stringent security when it’s time to push products or services into production. You can modify a strong security profile to be lax in the specific ways that enable DevOps to progress smoothly. But as developers will be working on machines that are secured with these “Dev” profiles, your organization can be assured that DevOps is secure throughout cycles. In other words, these security profiles make DevSecOps a reality for your organization.
Automation plays an essential role in applying these security profiles at scale throughout the various layers and processes of your organization. (We recommend reading this article for more info on why automation is crucial). Another important factor is having a central mechanism for deploying security profiles and getting visibility into both the overall and specific security state of your environment (more on this below).
I get that compliance, standards, and regulations tell me what to do, and that automated security profiles let me actually do it. But won’t it still take major effort and costs on my organization’s part to do all this?
Yes, but here’s the thing – you don’t have to do it yourself. At Cloud Raxak, our whole mission is to be the expert on knowing what to do and how to do proactive automated cloud security. And we can do it for you for much less effort and costs than your organization will likely spend doing it yourself.
We do all the heavy lifting in:
- Keeping up to date with new security and compliance standards/regulations/benchmarks/frameworks
- Translating these regulations into concrete, actionable security controls
- Creating both standard purpose security profiles (e.g. DISA-MCC, PCI-DSS, HIPAA), as well as working with you to create custom security profiles (e.g. company-specific DevOps profile)
- Updating these security profiles as changes to standards are made
- Automating the application of these profiles at scale and throughout the various layers of your organization
- Providing a central mechanism for applying security profiles and getting visibility into both the overall and specific security state of your environment
- Helping your organization be as proactive and automated as it can be about security, while drastically reducing both your security costs and your risk exposure
We also make it a point to focus on a security-first approach rather than a compliance-first approach. While a compliance-first approach gives you a good starting point, it may not ensure that you’re actually secure. Compliance regulations are typically broader in nature (e.g. industry-specific), but each organization will have its own individual security needs. A security-first approach puts compliance in context of the appropriate security and risk strategy for your organization. This approach will also speed your compliance efforts, reduce security complexity, and minimize security risks and costs.
To summarize, compliance, standards, and regulations are your friends. They give you guidance on what to do in order to be proactively secure. Cloud Raxak takes it a step further by doing all this for you in a fully automated manner, so you can be continuously secure without letting it slow you down.
In the next article, we’ll describe our model that translates your configuration practices to the risk exposure of your cloud environment. Borrowing from the methodology used by the financial community in transactional risk modeling, we map configuration management practices to the expected value of damage from security incidents. The model quantifies what we discussed in this previous article: that proactive automated cloud security drastically reduces your security risks and costs while enabling business growth.
Any questions?
Please feel free to contact us if you have any questions about using compliance, standards, and regulations to define a security and risk posture. We specialize in creating custom automated security profiles, so we’d be happy to work with you on defining a security posture and implementing it for your organization.
