Security Compliance for Cloud Assets

IBM Cloud, Intel, and Cloud Raxak Assured Security Compliance for Regulated Industries
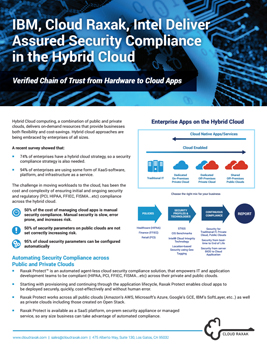
Cloud Raxak, IBM, and Intel have developed an industry first solution to provide Hardware Assured Security Compliance across the IBM hybrid cloud using a hardware basis of trust. The Raxak Protect security compliance platform leverages Intel® Cloud Integrity Technology, to automatically secure IBM Public and Private Private Clouds and meet the audit requirements of regulated industries including finance (FFIEC), retail (PCI), healthcare (HIPAA), and federal government (FISMA).
Raxak Protect can maintain a continuous chain of trust from the BIOS to the cloud application, enabling the secure configuration of the Host OS, hypervisor layer, and the guest VMs and Containers. This also enables continuous security compliance throughout the lifecycle of the assets from boot-time to end of life.
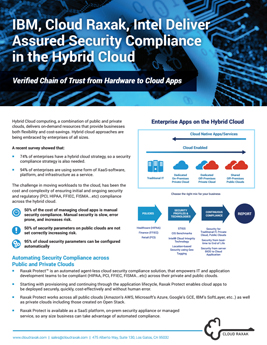
Raxak Protect Security Compliance Solution for IBM Cloud
Cloud Raxak has found that approximately 50% of the recommended security parameters are incorrectly configured when using the public cloud. However, 95% of these security parameters can be checked and configured automatically, significantly reducing security compliance costs and human error. Raxak Protect addresses the security compliance concerns of regulated industries including financial services, healthcare, retail, telecommunication, government, and life sciences by:
- securing cloud workloads using security profiles that meet regulated industry standards including FFIEC, PCI, HIPAA and FISMA.
- reducing costs and risk by automating monitoring, logging, audit ready reporting, and remediation throughout the lifecycle of the application.
- enabling developer innovation by applying security profiles in DevOps when the asset is created and then monitoring it throughout the app lifecycle.
- applying consistent security profiles across private and public clouds enabling the same level of data.
- providing the flexibility to deploy cloud security as a SaaS or onpremises appliance.
- one-touch security compliance through the IT service catalog to eliminate novice user risk.